We see lifecycles everywhere, product lifecycles, software development lifecycles, data lifecycles. They are a useful way to gain a high level understanding of something and to identify where we need to focus. We also have computer attack lifecycles, also known as Cyber Kill Chains. Cyber kill chains were developed from the analysis of countless attacks, identifying common patterns and actions of attackers.
They are useful in preparing defences against cyber attacks, post attack analysis and also used in penetration testing.
Cyber Kill Chain examples
There are a number of cyber kill chains available, each is different, but I’ll go through the common attack phases below. Some examples of cyber kill chains are:
This diagram of the FireEye cyber kill chain is a good example.
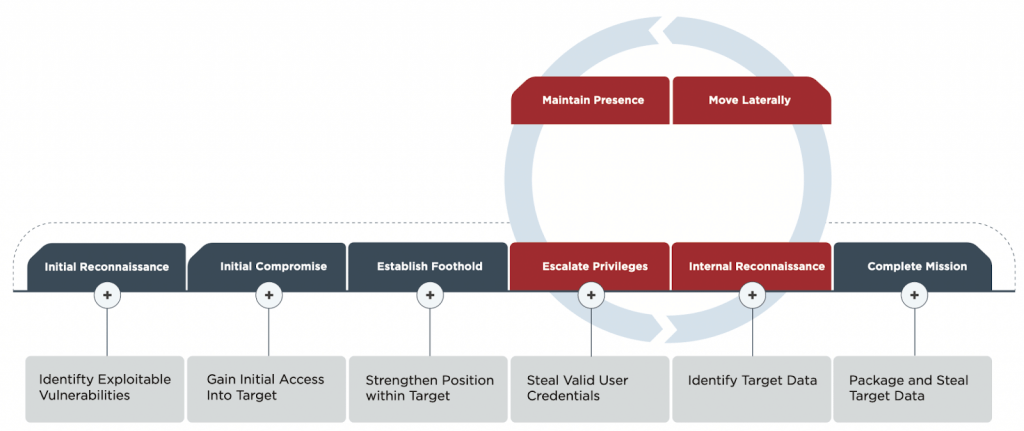
Common Attack Phases
1. Reconnaissance
Recon is learning as much as possible about a target. There are tech and non tech sources of information, but whatever the source of information, the outcome is the same: to discover an attack vector. It is difficult to mitigate against because you often don’t know it is happening.
2. Initial compromise
This is where the attacker first gets into your system, a common vector is phishing. Their goal is to run code on your system, it’s probably limited in what it can do but they will use it to build their attack.
Mitigation
- Patching (keeping software and OS up to date
- Use allow and block lists
- Network detection and prevention: signature detection; sand boxes; search for packers and compressors
- Security education and ownership for all staff.
3. Gain a foothold in your system
This is where the attacker solidifies their attack. They make sure they have the permissions they need, perhaps install a more comprehensive tool. You might wonder why they don’t just do this in stage 1, it’s to avoid detection and to hide their hand. A large package could raise suspicion and then their full capability would be exposed.
Mitigation
See stage 2.
4. Maintain & Solidify presence
The attacker now has a capability on your computer, but it is only in RAM, meaning it is not a permanent presence. They will now work to change that – establish a permanent presence and escalate privileges. A permanent presence is usually hidden in frequently accessed files, such as files that are run on startup or login. Permanence has a downside for the attacker though, it makes them more discoverable and can leave a history of infection which can be traced using forensics. Smart attackers will be selective with their permanence.
Escalating privileges will depend on the attack, the system and the target. Attackers can import further vulnerabilities or they can just ask for them. I recently undertook an attack on a business to test a vulnerability, all I had to do was ask their support team to add me as an admin.
5. Pivot
Once a system is compromised it will be used to achieve the attackers goal or as a stepping stone towards their goal. Actions could include: installing logic bombs; scraping personal documents; encrypting all of the files (ransomware); installing a keyboard logger or searching for other computers.
Mitigation
- Service or network level analysis
- Applying the ASD Essential Eight
- Privilege management: role based; principle of least privilege; zero trust
6. Action on objectives
This is the most varied stage, it’s where the attacker executes on their goal. It could be anything, including:
- Network movement (exploring the network). You may think this sounds like stage 5, but the attacker may be on a recon mission.
- Installing exploits for use in the future
- Installing an external connector or periodic polling
- Ransomware
- Data exfiltration
- Stealing business processes
- Stealing customer/supplier details
Mitigation
- Access logs for services/networks
- Data exfiltration logs
- Business processes (Opsec)
Conclusion
Of course attackers aren’t holding a copy of these kill chains and following them, there will be variations but the attack lifecycle is a powerful tool for understanding cyber attacks. It allows us to understand segment an attack and plan defences appropriate to each stage. This is useful because once you break the chain, the attack is thwarted. So if you can identify the stage an attack is at and have a response plan in place you can respond appropriately and destroy the attack.
Cyber kill chains also have applications in privacy, falling into the recon stage. We’ll at this more in the future.


