
The Telegraph Problem, MACS
Integrity of messages is a problem that is as old as messengers. In the old days, people would seal a message, they knew they couldn’t
Join me as I undertake my Masters of Cyber Security

Integrity of messages is a problem that is as old as messengers. In the old days, people would seal a message, they knew they couldn’t

Risk is something we deal with all of the time, and humans are good at assessing some risks and bad at assessing others. But, we

A long post today, we’ll recap of classic ciphers, look at the history of modern symmetric ciphers. Finally we’ll look at entropy, a way of

Now that we covered asymmetric cryptography and and how RSA works, there’s nothing like working through equations to understand them. So let’s do some practice

We learnt about the basics of cryptography when we learnt about ciphers and secrets. These involve symmetrical cryptography, meaning that the person doing the enciphering

Merkle puzzles are the first publicly recorded example of asymmetric cryptography. It was devised by Ralph Merkle, he was trying to work out a way

The start of a new course this week – Intro to Security Engineering, where we look at applying engineering principles to security. Although cyber security

This week we were tasked with investigating how an engineering problem was solved in another discipline. For my engineering problem, I’ve chosen the dome of

Shifting Security Left is a paradigm that encourages a proactive, rather than reactive – approach to security. The term is in reference to the software

An interesting and concerning security in the news this week. It has been alleged that Israelli Cyber Surveillance Company, NSO’s software has been used by

A data lake is a lot of data. Lots of pieces of useless information, all floating around made useful by proximity and manipulation. As security

I’ve noticed an ongoing pattern for the NSW government. They don’t appear to be able to keep data safe. It was reported on 1 September

Not many people like the idea of state surveillance. But first we need to recognise that surveillance can have good and bad aspects – it

A one time pad is what’s known as a perfect cipher. Without the key it is uncrackable and can’t be brute forced. The penny dropped

Identity theft is a major problem. It occurs when criminals collect enough of your personal information to convince people that they are you. What sort

Data hungry website We all know that websites are tracking us all of the time, as I mentioned the data tracking economy when I explored

Considering what I have learnt this week (in this post), I’ve decided it’s time to cast a critical eye over my own password management practices.

There has been a fair bit of conjecture in the press about Chinese backed cyber attacks in recent times, but there has been no evidence

How do people treat passwords? The Avast report about Americans and passwords makes for disturbing reading. https://press.avast.com/83-of-americans-are-using-weak-passwords Many Americans use personal information such as partner’s
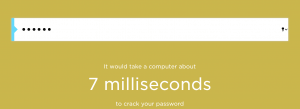
What is the longest it would take someone to brute force a password based on certain criteria? The worst case for the hacker? I’ve wondered

This week we looked at classical ciphers. I enjoyed this, looking at the ingenious ways that clever people have come up with hiding messages in

This week we were challenged to physically destroy some data. I’ve chosen to unshred a document. Not a special document , just some junk mail

The problems with secrets Secrets are interesting. People want to keep secrets, people want to find secrets, people want to share them. They are important

Classified details of the UK Challenger 2 Tank were leaked on a game forum for the game War Thunder. What was Happened The AESP (Army

A pile of classified UK documents were found in a “in a soggy heap behind a bus stop in Kent” on 22 June 2021. The

For an activity this we were tasked with finding an example of an insider attack. An insider attack could be carried out by a true

According to The Age, the government is considering making company directors liable for cyber attacks. With cyber crime costing Australia around $3.5 billion a year,

According to The ABC, State-sponsored cyber operations have doubled in the last two years. This is a scary statistic, we hear about the next war

While learning about patterns in security, a recent news story came to mind when scope creep was mentioned -specifically systems and data being created or

I decided to look at the data Facebook holds about me. I was surprised how easy it was to get my information from Facebook and

Introduction Want to know how to protect yourself and limit the damage caused by a cyber attack? The Essential Eight was released by the Australian

Welcome to my cyber security blog! A quick introduction before we start. I’m Luke Hally, I’ve had a varied career in digital: making websites for
© Copyright 2021, Luke Hally