
Learning from others
This week we were tasked with investigating how an engineering problem was solved in another discipline. For my engineering problem, I’ve chosen the dome of
Join me as I undertake my Masters of Cyber Security

This week we were tasked with investigating how an engineering problem was solved in another discipline. For my engineering problem, I’ve chosen the dome of

Shifting Security Left is a paradigm that encourages a proactive, rather than reactive – approach to security. The term is in reference to the software

A data lake is a lot of data. Lots of pieces of useless information, all floating around made useful by proximity and manipulation. As security

Not many people like the idea of state surveillance. But first we need to recognise that surveillance can have good and bad aspects – it

A one time pad is what’s known as a perfect cipher. Without the key it is uncrackable and can’t be brute forced. The penny dropped

Identity theft is a major problem. It occurs when criminals collect enough of your personal information to convince people that they are you. What sort

Data hungry website We all know that websites are tracking us all of the time, as I mentioned the data tracking economy when I explored

Considering what I have learnt this week (in this post), I’ve decided it’s time to cast a critical eye over my own password management practices.

How do people treat passwords? The Avast report about Americans and passwords makes for disturbing reading. https://press.avast.com/83-of-americans-are-using-weak-passwords Many Americans use personal information such as partner’s
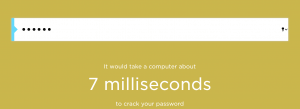
What is the longest it would take someone to brute force a password based on certain criteria? The worst case for the hacker? I’ve wondered
© Copyright 2021, Luke Hally