
Social engineering hack
“ Social engineering is an extremely effective technique used by hackers worldwide to compromise internal systems and proprietary information assets. In fact, it’s one of
Join me as I undertake my Masters of Cyber Security

“ Social engineering is an extremely effective technique used by hackers worldwide to compromise internal systems and proprietary information assets. In fact, it’s one of

On 29 April 2018, NewCorp journalist, Annika Smethurst, reported that the federal government was wanting to expand its powers to spy on Australian citizens. This

I’ve had a couple of opportunities to apply what I have learnt in the real world this week. Estimating Attacker Power This degree has affected

We authenticate to solve real world problems. For example I want me to be able to access my bank account and I don’t want anyone

Authentication is proving who you are. Not to be confused with authorisation, which is having permission to access or use something. In security we often

Thanks to my involvement in fintech, I’ve been around the edges of bitcoin and blockchain for a while Traditional money relies on a trusted third

There’s a lot to remember about hashes, so I’m bringing the definitions into one place as a reference. Term Definition Avalanche effect Small changes in
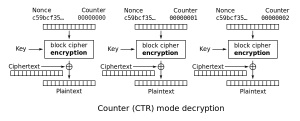
DES (Data Encryption Standard) and AES (Advance Encryption Standard) are both block ciphers. The message is broken into blocks and each block is encrypted and

What are type I and type II errors? They sound fancy but are quite simple to understand and are a good way to look at

Encryption is the glamourous part of confidentiality, today we will look at hashes. We’ll cover regular and cryptographic hashes, a bit of history then we’ll
© Copyright 2021, Luke Hally